VNC Resolver: Difference between revisions
m (1 revision imported) |
(the march 2nd incident) |
||
| (6 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
'''VNC Resolver''', formerly known as "VNC Roulette" and "VNC Funland", is a tool that displays random insecure VNC servers. It is similar to sites like srsly.de, WorldofVNC, Shodan, and others. It was created in late 2015. |
'''VNC Resolver''', formerly known as "VNC Roulette" and "VNC Funland", is a tool that displays random insecure VNC servers. It is similar to sites like srsly.de, WorldofVNC, Shodan, and others. It was created in late 2015. |
||
The first scan was done in December 2015. The latest scan was done on |
The first scan was done in December 2015. The latest scan was done on May 24, 2022 and ended on May 27, 2022 |
||
You can browse the current scan by going [https://computernewb.com/vncresolver/browse/ here]. It is also available through [[CollabBot]] by typing +vnc. |
You can browse the current scan by going [https://computernewb.com/vncresolver/browse/ here]. It is also available through [[CollabBot]] by typing +vnc. |
||
| Line 8: | Line 8: | ||
'''VNC Resolver''' is currently a part of the CollabBot bot on the CollabVM Discord. It also has a web interface (linked above). |
'''VNC Resolver''' is currently a part of the CollabBot bot on the CollabVM Discord. It also has a web interface (linked above). |
||
VNC Resolver works by portscanning the entire internet for ports 5900-5910, and then a script attempts to take a screenshot of the found servers. If it times out or is passworded, the server is skipped, but if a connection is successful, a screenshot is taken and it is added to the database. |
VNC Resolver works by portscanning the entire internet for various ports (usually 5900 - 5910, but smaller ASNs usually get more ports scanned), and then a script attempts to take a screenshot of the found servers. If it times out or is passworded, the server is skipped, but if a connection is successful, a screenshot is taken and it is added to the database. |
||
The scripts for VNC Resolver were released on September 27, 2018 and may be downloaded [https://cdn.discordapp.com/attachments/256538008126226432/511269629914513408/VNC-Scanner.7z here]. ('''WARNING''': Port scanning the entire internet WILL GET YOUR IP LISTED IN MOST MAJOR BLACKLISTS. This will likely cause you to be banned from certain sites. Many major ISPs across the world also ban portscanning entirely, and may terminate your service if they catch you. Use a VPS if you're going to run this.) |
The scripts for VNC Resolver were released on September 27, 2018 and may be downloaded [https://cdn.discordapp.com/attachments/256538008126226432/511269629914513408/VNC-Scanner.7z here]. ('''WARNING''': Port scanning the entire internet WILL GET YOUR IP LISTED IN MOST MAJOR BLACKLISTS. This will likely cause you to be banned from certain sites. Many major ISPs across the world also ban portscanning entirely, and may terminate your service if they catch you. Use a VPS if you're going to run this.) |
||
| Line 31: | Line 31: | ||
Following the incident, the VNC Roulette was shut down in order to make improvements, and it has returned sporadically, although usually going down for technical reasons. |
Following the incident, the VNC Roulette was shut down in order to make improvements, and it has returned sporadically, although usually going down for technical reasons. |
||
Another incident occured on March 2, 2024 involving the [https://fedi.computernewb.com/@vncresolver/112026570733053536 VNC Resolver Mastodon bot], where an unknown user connected to a pool controller in Poland. They then, attempted to mess with the settings but then the device got DDoSed and [https://files.catbox.moe/2u2ejg.png it broke]. |
|||
==Gallery of VNCs== |
==Gallery of VNCs== |
||
<gallery> |
<gallery> |
||
Blank.jpg|The most common type of VNC you'll find. |
File:Blank.jpg|The most common type of VNC you'll find. |
||
File:Linux login.jpg|The second most common. Text in terminal may vary. |
|||
File:Chinese gamer.jpg|The third most common. The desktop may vary. |
|||
File:Windows Server 2008 VNC.jpg|The fourth most common. Usually in Japanese. |
|||
Israeli.jpg|The fifth most common. |
File:Israeli.jpg|The fifth most common. |
||
Danfoss.jpg|The sixth most common. |
File:Danfoss.jpg|The sixth most common. |
||
File:Industrial 1.jpg|Industrial machine |
|||
File:Industrial 2.jpg|Another industrial machine |
|||
File:Industrial 3.jpg|Another industrial machine |
|||
File:Industrial 4.jpg|Another industrial machine |
|||
File:Industrial 5.jpg|Another strange industrial machine |
|||
File:Industrial 6.jpg|Another industrial machine in Polish |
|||
File:Do not shoot.jpg|An industrial machine with a vaguely funny message. This was later changed to "Safe to Shoot." |
|||
TicTacToe.jpg|Someone playing Tic Tac Toe against a computer (and losing...) |
File:TicTacToe.jpg|Someone playing Tic Tac Toe against a computer (and losing...) |
||
NT 4.jpg|Hotel POS software running on Windows NT 4 |
File:NT 4.jpg|Hotel POS software running on Windows NT 4 |
||
Another NT4.jpg|Some more NT 4 software |
File:Another NT4.jpg|Some more NT 4 software |
||
Windows CE.jpg|Windows CE Logon Screen |
File:Windows CE.jpg|Windows CE Logon Screen |
||
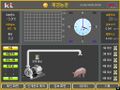
Pig Farm.jpg|Korean Pig Farm |
File:Pig Farm.jpg|Korean Pig Farm |
||
Enpass.jpg|Someone running a "password generator" on their open VNC |
File:Enpass.jpg|Someone running a "password generator" on their open VNC |
||
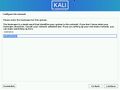
Kali.jpg|Someone installing Kali |
File:Kali.jpg|Someone installing Kali |
||
198.23.239. |
File:198.23.239.186 5900.jpg|Someone viewing their Gmail |
||
Messy.jpeg|A very messy desktop |
File:Messy.jpeg|A very messy desktop |
||
File:Very large desktop.jpg|A large desktop |
|||
Nvidia.jpg|Nvidia-themed Ubuntu login |
File:Nvidia.jpg|Nvidia-themed Ubuntu login |
||
File:Mac or BSD error.jpg|An error on BSD or Mac OS |
|||
File:7 login with Mark.jpeg|Chinese Windows 7 login with a user named "Mark" |
|||
File:Hebrew error.jpg|An error on some Hebrew software |
|||
File:Hungarian terminal.jpg|Terminal connecting to some IP address |
|||
UOS.jpg|Chinese Linux distribution |
File:UOS.jpg|Chinese Linux distribution |
||
File:Phone 1.jpg|An Android phone |
|||
File:Phone 2.jpg|Another Android phone |
|||
Panic.jpg|A kernel panic |
File:Panic.jpg|A kernel panic |
||
Hacked.jpg|A seemingly hacked Linux root shell |
File:Hacked.jpg|A seemingly hacked Linux root shell |
||
18.132.67. |
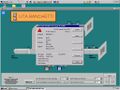
File:18.132.67.12 5900.jpg|Bank thingy? |
||
95.125.182. |
File:95.125.182.61 5900.jpg|Guy watching the world die on a industrial machine |
||
106.6.202. |
File:106.6.202.196 5901.jpg|Quick! They are on to me!! Better turn off my computer!!! |
||
202.59.172. |
File:202.59.172.138 5900.jpg|Something that looks like a UEFI firmware settings menu |
||
File:No OS 1.jpg|A computer without an operating system |
|||
File:No OS 2.jpg|Another computer without an operating system |
|||
File:Opensuse 1.jpg|An OpenSUSE login screen. Variants are plentiful. |
|||
File:Display manager.jpg|A Linux display manager for a library computer |
|||
File:Debian 1.jpg|A Debian computer that has been logged into |
|||
File:Root console.jpg|A Linux root console that has executed ip route |
|||
Cirros.jpg|A Cirros Linux login screen. Very common. |
File:Cirros.jpg|A Cirros Linux login screen. Very common. |
||
File:Obscure bootloader.jpg|An obscure bootloader |
|||
File:Linux update.jpg|Somebody updating their Linux system |
|||
File:Happy hacking.jpg|A program/OS which seems to be hacking-related |
|||
File:Linux warning.jpg|A Linux login screen with a warning |
|||
File:Ubuntu Trusty.jpg|An Ubuntu 14.04 login screen |
|||
File:Mysterious VNC.jpg|A cryptic VNC server |
|||
Marbella.jpeg|A Spanish VNC server |
File:Marbella.jpeg|A Spanish VNC server |
||
Open vnc ipgone.jpg|Strange iPhone VNC |
File:Open vnc ipgone.jpg|Strange iPhone VNC |
||
TeamViewer VNC.jpg|An insecure VNC showing TeamViewer login. Funnily enough, the client name was "kk-security194". |
File:TeamViewer VNC.jpg|An insecure VNC showing TeamViewer login. Funnily enough, the client name was "kk-security194". |
||
CampSwift.jpg|A VNC that should definitely not be online. |
File:CampSwift.jpg|A VNC that should definitely not be online. |
||
Dickbutt.jpg|A VNC which is just Dickbutt. |
File:Dickbutt.jpg|A VNC which is just Dickbutt. |
||
Kitchenbox.jpg|Interesting kitchen IoT(?) VNC |
File:Kitchenbox.jpg|Interesting kitchen IoT(?) VNC |
||
WhatTheHell.jpg|VNC of an sewage company that manages water pipes. |
File:WhatTheHell.jpg|VNC of an sewage company that manages water pipes. |
||
GameServer.jpg|An insecure VNC hosting a server for the game "Subsistence". |
File:GameServer.jpg|An insecure VNC hosting a server for the game "Subsistence". |
||
SecFox.jpg|Login screen for a Linux distribution called "SecFox OS", running on a Chinese server. No information about this OS appears to be present online. |
File:SecFox.jpg|Login screen for a Linux distribution called "SecFox OS", running on a Chinese server. No information about this OS appears to be present online. |
||
BillboardVNC.jpg|A VNC that appears to belong to a billboard or some digital signage. |
File:BillboardVNC.jpg|A VNC that appears to belong to a billboard or some digital signage. |
||
Glitched VNC.jpg|Broken turkish VNC server sending invalid compression data, resulting in this broken mess. |
File:Glitched VNC.jpg|Broken turkish VNC server sending invalid compression data, resulting in this broken mess. |
||
File:Bitcoin Miner.jpg|A VNC with 4 GPUs mining Bitcoin. |
|||
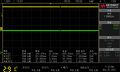
File:DSOX1202A Oscilloscope.jpg|A DSOX1202A Oscilloscope by Keystone with an Open VNC |
|||
File:Port 15900.jpg|A Windows 7 VM running on Port 15900. Always remember: Security by obscurity is not security. |
|||
File:Restaurant PoS.jpg|Restaurant PoS Software |
|||
File:Android 3.jpg|An Android phone |
|||
File:FunnyLockWallpaper.jpg|A very good lock screen wallpaper. |
|||
File:Blueprints.jpg|Some sort of blueprints? |
|||
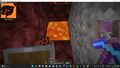
File:Minecraft Gamer.jpg|Someone playing Minecraft |
|||
File:VB6 Monitor.jpg|Some monitoring software? |
|||
File:Vnc testing in progress.webp|Testing what? |
|||
</gallery> |
</gallery> |
||
Latest revision as of 16:50, 2 March 2024
VNC Resolver, formerly known as "VNC Roulette" and "VNC Funland", is a tool that displays random insecure VNC servers. It is similar to sites like srsly.de, WorldofVNC, Shodan, and others. It was created in late 2015.
The first scan was done in December 2015. The latest scan was done on May 24, 2022 and ended on May 27, 2022
You can browse the current scan by going here. It is also available through CollabBot by typing +vnc.
VNC Resolver
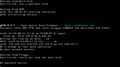
VNC Resolver is currently a part of the CollabBot bot on the CollabVM Discord. It also has a web interface (linked above).
VNC Resolver works by portscanning the entire internet for various ports (usually 5900 - 5910, but smaller ASNs usually get more ports scanned), and then a script attempts to take a screenshot of the found servers. If it times out or is passworded, the server is skipped, but if a connection is successful, a screenshot is taken and it is added to the database.
The scripts for VNC Resolver were released on September 27, 2018 and may be downloaded here. (WARNING: Port scanning the entire internet WILL GET YOUR IP LISTED IN MOST MAJOR BLACKLISTS. This will likely cause you to be banned from certain sites. Many major ISPs across the world also ban portscanning entirely, and may terminate your service if they catch you. Use a VPS if you're going to run this.)
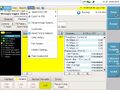
Types of VNC's
- Black screens
- Dead VNC's (Possibly due to dynamic IP's)
- Servers
- Embedded computers
- Login screens
- Honeypots
- Internet cafe machines
- Asian gamers?
- Billboards
- XSCREENSAVER
Incident
An incident occurred on February 21 2016 involving VNC Roulette, in which Damian connected to an insecure VNC which was connected to a pool in a small town in New Jersey. Guest1337 attempted to set the pH levels to potentially lethal levels, but was stopped by both the software and an administrator before any harm could actually be done.
It should be noted that the user in question was doing this from his own computer on CollabVM.
Following the incident, the VNC Roulette was shut down in order to make improvements, and it has returned sporadically, although usually going down for technical reasons.
Another incident occured on March 2, 2024 involving the VNC Resolver Mastodon bot, where an unknown user connected to a pool controller in Poland. They then, attempted to mess with the settings but then the device got DDoSed and it broke.
Gallery of VNCs
-
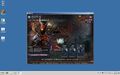
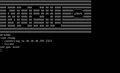
The most common type of VNC you'll find.
-
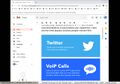
The second most common. Text in terminal may vary.
-
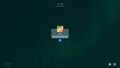
The third most common. The desktop may vary.
-
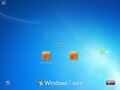
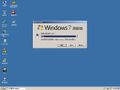
The fourth most common. Usually in Japanese.
-
The fifth most common.
-
The sixth most common.
-
Industrial machine
-
Another industrial machine
-
Another industrial machine
-
Another industrial machine
-
Another strange industrial machine
-
Another industrial machine in Polish
-
An industrial machine with a vaguely funny message. This was later changed to "Safe to Shoot."
-
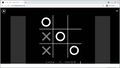
Someone playing Tic Tac Toe against a computer (and losing...)
-
Hotel POS software running on Windows NT 4
-
Some more NT 4 software
-
Windows CE Logon Screen
-
Korean Pig Farm
-
Someone running a "password generator" on their open VNC
-
Someone installing Kali
-
Someone viewing their Gmail
-
A very messy desktop
-
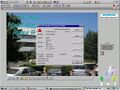
A large desktop
-
Nvidia-themed Ubuntu login
-
An error on BSD or Mac OS
-
Chinese Windows 7 login with a user named "Mark"
-
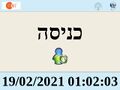
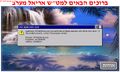
An error on some Hebrew software
-
Terminal connecting to some IP address
-
Chinese Linux distribution
-
An Android phone
-
Another Android phone
-
A kernel panic
-
A seemingly hacked Linux root shell
-
Bank thingy?
-
Guy watching the world die on a industrial machine
-
Quick! They are on to me!! Better turn off my computer!!!
-
Something that looks like a UEFI firmware settings menu
-
A computer without an operating system
-
Another computer without an operating system
-
An OpenSUSE login screen. Variants are plentiful.
-
A Linux display manager for a library computer
-
A Debian computer that has been logged into
-
A Linux root console that has executed ip route
-
A Cirros Linux login screen. Very common.
-
An obscure bootloader
-
Somebody updating their Linux system
-
A program/OS which seems to be hacking-related
-
A Linux login screen with a warning
-
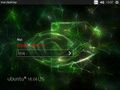
An Ubuntu 14.04 login screen
-
A cryptic VNC server
-
A Spanish VNC server
-
Strange iPhone VNC
-
An insecure VNC showing TeamViewer login. Funnily enough, the client name was "kk-security194".
-
A VNC that should definitely not be online.
-
A VNC which is just Dickbutt.
-
Interesting kitchen IoT(?) VNC
-
VNC of an sewage company that manages water pipes.
-
An insecure VNC hosting a server for the game "Subsistence".
-
Login screen for a Linux distribution called "SecFox OS", running on a Chinese server. No information about this OS appears to be present online.
-
A VNC that appears to belong to a billboard or some digital signage.
-
Broken turkish VNC server sending invalid compression data, resulting in this broken mess.
-
A VNC with 4 GPUs mining Bitcoin.
-
A DSOX1202A Oscilloscope by Keystone with an Open VNC
-
A Windows 7 VM running on Port 15900. Always remember: Security by obscurity is not security.
-
Restaurant PoS Software
-
An Android phone
-
A very good lock screen wallpaper.
-
Some sort of blueprints?
-
Someone playing Minecraft
-
Some monitoring software?
-
Testing what?